Growing up, Michael Nowatkowski had a passion for building things that made his life easier.
Once, he built a string system in his bedroom, connecting the top of his closet door to the door frame. He then tied a counterweight to the other side of the string to automatically shut his closet door. He was only 8 — and had no internet or YouTube to consult.
“I was lazy as a kid, and it was a lot of effort to close my closet door,” he said, his eyes twinkling at the memory. “I don’t know… I always just enjoyed tinkering and building things.”
This passion for building physical systems would later define his career path. An associate professor of information security at Augusta University, Nowatkowski would eventually use his ability to solve problems to guide him through his current research quest: safeguarding the lives of millions of patients who depend on wireless-connected medical devices to heal or survive.
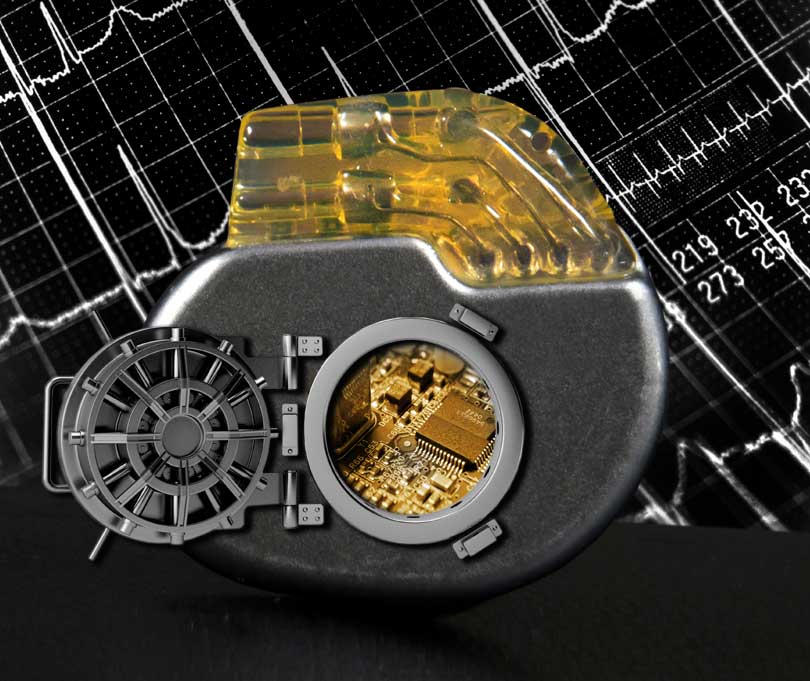
A cautionary tale about an unlocked door
A man in his late 60s decides to take on a stressful job despite a family history of heart disease and after surviving four heart attacks. As a precaution, he gets a pacemaker implanted in his chest to control his heartbeat through low-voltage electrical shocks — a decision that could potentially save his life.
The problem, however, lies in the device’s wireless function, which is a door easily opened by hackers intent on causing bodily harm. By modifying the electrical pulse that controls the man’s heartbeat, they could cause a major heart attack.
The risk of this happening might seem slim for most of us, but in this case, the man in question is the vice president of the United States — and not a fictional one, but the real one.
In 2007, then Vice President Dick Cheney actually had the wireless function of his pacemaker turned off for fear of an assassination attempt.
When Cheney made this alarming revelation in an interview with 60 Minutes in 2013, Nowatkowski — like other cybersecurity professionals — already knew about the potential security flaws of medical devices.
At the time, Nowatkowski was an associate professor of electrical engineering and computer science at the U.S. Military Academy at West Point. There, displaying the same enthusiasm and ingenuity he had as a child, he taught electrical engineering courses, helping students build electric circuits through fun, hands-on projects like building nightlights that turned on automatically when it got dark or karaoke machines that could work with a standard MP3 file.
A lieutenant colonel in the U.S. Army with a doctorate in electrical and computer engineering, Nowatkowski did not want to just build electrical systems. He wanted to build chips that were secure and wanted to teach his students that concept.
“I enjoy looking at the hardware side of cybersecurity — how do we protect the devices physically and how can we configure the hardware in the system to make it more secure,” he said.
Cheney’s revelation made a powerful case for protecting these vulnerable devices.
Although Nowatkowski was not yet researching the flaws of medical devices at that time, his 2016 move from West Point to Augusta University, Georgia’s only public academic health center, would change that.
“Seeing the close relationship we have with the hospital and the health care profession — I think it really caused me to start thinking about, ‘let’s look at medical devices as a potential area of research,’” he said.
Locking a door
Once, Americans felt comfortable leaving their front doors unlocked, but times have changed.
Times have also changed when it comes to medical devices, but technology hasn’t kept pace. For most of these devices, locks don’t exist.
“These were meant to be used in a controlled environment where you wouldn’t just have somebody walk up to the device and access it,” Nowatkowski said. “But they are wireless-enabled now, so somebody could be sitting in the waiting room or the lobby and potentially get in wirelessly to these devices.”
Through a review of the literature, Nowatkowski found that these medical devices have authentication flaws, including not requiring a password to access them.
Having no password is the same as never locking your front door.
In other cases, devices do have an authentication process, but the password is written on the manual and cannot be changed.
That is the same as locking your front door but leaving the key under the rug with a sign that says “The key is right here.”
What could hackers do with that key?
Best-case scenario? They could easily get into these devices and steal people’s medical information, including names, birth dates, insurance and prescription information, and Social Security numbers.
Worst-case scenario? Cyber criminals could modify the data they found in the devices, including increasing a pacemaker’s shock intensity or altering the dosage in IV pumps or the insulin amount in insulin pumps.
The result would be Cheney’s nightmare scenario: death by cyberattack.
Given the risks, Nowatkowski wants to secure the authentication door. But to fix the problem, he first needs to find the flaws in the devices — a process he first learned when he was a child.
“I remember my grandfather was always fixing things,” he said. “The TV would stop working, and he’d tear the back of the TV open and pull some of the tubes out. We’d go to the store and put them in the little tube tester machine and would figure out which one was not working…. I thought it was really neat that he was able to do something like that.”
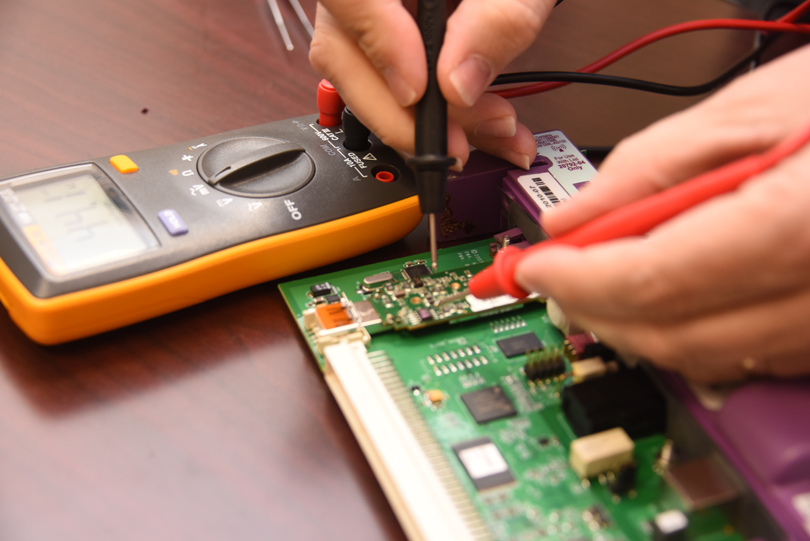
Following that same process in his current research, Nowatkowski will first disassemble 10 single- and 3 triple-channel IV pumps, analyze and test their chips, and identify their security flaws.
Only then will he be in a position to fix the problem and make those devices more secure.
Once he identifies the flaws, he will compare his findings with the literature. If there is a match, he will use the same tools and processes to analyze other medical devices — the ones people are bringing home.
“I would hate to think that there are folks out there that would indiscriminately hack into people’s medical devices and try to kill them,” Nowatkowski said. “I would almost think that the danger is more in the bad guys trying to get in and steal information.”
By connecting their medical devices to their home network — the same one their personal computers are already connected to — people are putting their medical information at risk.
“When they are going out and clicking on links and introducing vulnerabilities to their home computer, there’s a chance that those vulnerabilities could then extend access to their medical devices,” Nowatkowski said. “These devices are going to be sending data back to their caregiver, potentially to their insurance company, potentially to the device manufacturer, so there’s a lot of different connections that these devices will have for sending and receiving data.”
In an unsecure home network, hackers can easily intercept these connections and read people’s medical information.
Why would they want this type of information? Because it is 5 to 10 times more valuable than your credit card information, Nowatkowski said.
“You are not likely going to change your insurance company, or you are not going to change your Social Security number,” he said. “It’s much harder to change your medical information than it is to get a new credit card.”
Securing that medical information is fundamental for Nowatkowski’s research.
Though Cheney’s concerns were valid, for most of us the risk of medical harm inflicted by hackers is far less than the risk of not relying on medical devices.
“You are better off having your medical device and being healthy,” Nowatkowski said. “I think the risk of you having serious problems because of the medical condition is higher than the risk of you being affected by a hacker that’s hacking into your medical device.”

Locking other doors
Because of their portability, convenience and wireless connectivity, new medical devices have become part of the Internet of Things — a network of computerized, everyday devices like smart TVs, thermostats and light bulbs that supposedly makes people’s lives easier.
All these systems have the same basic construct, so Nowatkowski’s research on medical devices has broader implications for the future of the Internet of Things.
“If we can … figure out principles for secure design of those medical devices, the long-range goal is to apply those same principles to all sorts of small embedded-system devices,” Nowatkowski said.
His research, therefore, would eventually make it more difficult for a criminal to hack into your home network and watch you through your baby monitor or security cameras or even gain control over your thermostat or smart TV.
For now, however, the Internet of Things still presents a great risk to users by giving hackers multiple entry points into a home network.
“Manufacturers for these devices are trying to get these products to market as quickly as they can for as cheaply as they can,” Nowatkowski said. “The secure design of these devices is really an afterthought.”
With his research, he hopes to change this reality.






